Y’know, any time there’s a week with a story about Justin Bieber’s latest meltdown (which is pretty much every week), it’s nearly impossible to compete. The dog and pony show known as Bieber pretty much screams for a movie of the week, and nothing else that crops up in the news is nearly as funny as the Beebs’ impending fall from grace. But then governments, which are nearly as talentless as Beebs and at least as laughable as his hair, prove that there is a place in the comic kingdom for the wisdom, or lack thereof, of the silly service.
Recently, we saw how a big telecom found a cheap yet effective way of dealing with an attack, when Telecom NZ decided the best way to deal with a spam attack was to cancel the account passwords of more than 60,000 of its users. Yes, in a world where shock and awe is often confused by schlock and aww, one of New Zealand’s largest telcos decided to take the easy way out rather than fix the problem, in the process angering a large number of its users, and rightfully so. And while Telecom NZ isn’t a government agency, it is a bureaucracy, and it seemed unlikely that this level of boneheadedness could be topped by another bureaucracy. Well, never one to turn down a challenge, the German government has found a way to stick its tongue out at every other Darwin Award winner this month.
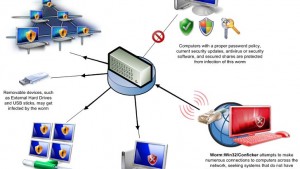
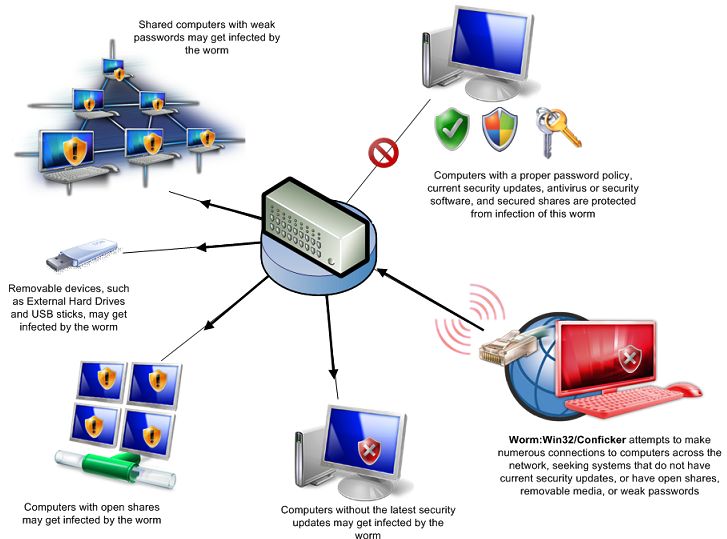
The story goes like this, according to the Register: the German education ministry, so the story goes, discovered that 170 brand new PCs were infected with the Conficker worm. “It emerged this week that a grand total of 170 PCs and servers at German teacher training institutes in Schwerin, Rostock and Greifswald were dumped soon after they became infected with the notorious Windows worm in September 2010. The decision cost German taxpayers €187,300 (£158,291).”
Now, as you probably know, Conficker is a nasty little piece of malware that shouldn’t be left alone with a PC, let alone 170 of them. One of the most pervasive and devastating known worms, Conficker was discovered in 2008 and currently infects millions of computers in more than 200 countries. Due to its sophistication, the worm is generally believed to be the work of an Eastern European crime syndicate, because a vast amount of resources would be required to develop it, and the little bugger is extremely difficult to detect and destroy. And Conficker left an indelible mark. According to the Register, “the peak zombie headcount created by the botnet peaked at over six million PCs, more than enough to create all sorts of mayhem. Backdoored PCs were, of course, wide open to secondary infection but not much malfeasance along these lines actually took place.”
Now, that may sound like reason enough to call it a day and bin €187,300 worth of computer equipment, right? Not so fast. First, if the government agency had decided to sanitize the systems, it would have been considerably cheaper than trashing them and purchasing new ones. In an article at heise.de and according to an audit report, cleaning the malware would have cost around €130,000, a difference of €57,000, and that’s not chump change.
Open Door Policy
According to the Register, a report by auditors at the State of Mecklenburg-Vorpommern, states “that the teacher training colleges had left themselves wide open to attack by failing to create a up-to-date security policy.” Well, duh. Wish that were the first time I’d heard of an organization which either didn’t have current policies or chose to ignore them. Nevertheless, the auditors weren’t able to apportion blame and concluded that “It remains unclear if the anti-virus product had some issues, or if the outbreak was caused by technical or human failure.”
Indeed. Security firm Sophos reached their own conclusions, pointing out that a little antivirus software and a properly implemented backup policy would have averted the disaster to taxpayers’ wallets. It appears that the agency has some explaining to do, as an open door policy for spammers and malware rarely lends itself to a happy conclusion.
Windows PCs infected with Conficker’s C variant download Spyware Protect 2009, which is good old fashioned scareware, and Waledac, everyone’s least favorite botnet client. The spread of Conficker led to a partnership between Microsoft and several major players in the information security field, known as the Conficker Working Group. To date, the group has been moderately successful in neutralizing parts of Conficker’s control system.