 Just in case you thought that winter had set in, a new year had begun, and everything was right with the world once again, we have some rough news for you. 2015’s not going to be sunshine and lollipops, and the criminals are at it already, disturbingly so. This week, the cybersphere is reporting that a variant of Curve-Tor-Bitcoin (CBT) is being distributed as a spam campaign; and before you shrug it off as yet another sensational attempt by cybercrooks to compromise your well-oiled security methods, remember that your users aren’t nearly as savvy or in touch with current affairs as you are.
Just in case you thought that winter had set in, a new year had begun, and everything was right with the world once again, we have some rough news for you. 2015’s not going to be sunshine and lollipops, and the criminals are at it already, disturbingly so. This week, the cybersphere is reporting that a variant of Curve-Tor-Bitcoin (CBT) is being distributed as a spam campaign; and before you shrug it off as yet another sensational attempt by cybercrooks to compromise your well-oiled security methods, remember that your users aren’t nearly as savvy or in touch with current affairs as you are.
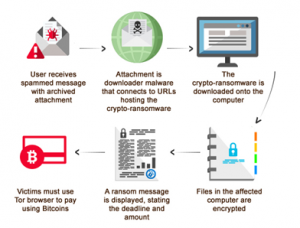
CBT-Locker, also known as Critroni, is ransomware, and while there are many and varied threats out there, none are quite as irritating as ransomware. If you’re anything like us, the mere thought of having your data sitting there in front of you and yet so far away is a kind of torture that makes us want to petition the Geneva Conventions. Once installed on your system, the ransomware makes your data inaccessible until you pay up, and even then, there’s no guarantee that the ‘kidnapper’ will do the right thing, a toss-up considering the scumlike low moral character that put your data at risk in the first place.
But we digress. CBT-Locker uses Tor, an anonymity network that channels user traffic through a network of more than five thousand hosts. It conceals the user’s location and usage history, making it virtually impossible to track anyone using the network. This one hurts a bit, too, because Tor is intended (by Tor’s own admission) to defend against “personal freedom and privacy.”
CBT-Locker was first discovered in the middle of 2014, and while the transmission is invisible thanks to Tor, the payload itself encrypts data on the target computer using elliptic curve cryptography, which its creator “claims is significantly faster than encryption schemes used by other ransomware threats,” according to PC World. The software is more powerful than Cryptolocker, which the US Department of Justice shut down in May, 2014. Its creator has been peddling the ransomware to other criminals, the magazine points out, “on Russian-language forums since the middle of June and it seems that he’s been trying to fix most of Cryptolocker’s faults.”
Once the software’s been installed on the target computer, the criminal contacts the infected party with the sales pitch. “Like Cryptolocker, Critroni generates a public and private key pair for every infected system. The public key is stored on the infected computer and given to the victim, who is then asked to pay a ransom in Bitcoin in order to recover the files.” The private key is kept safe and sound on a C&C server that can only be accessed through the Tor network, again ensuring that the criminal can avoid being traced by law enforcement.
If you followed the Cryptolocker story, you know that knocking the C&C infrastructure offline rendered Cryptolocker inert. Unfortunately, CBT-Locker isn’t nearly as easy to kill:
“To prevent a similar takedown Critroni was designed to complete the file encryption operation locally before connecting to the command-and-control server. This also makes it hard for network security products to detect it early and block it by analyzing traffic.
Blocking Tor traffic only prevents the user from paying, not the program from functioning, the Critroni author said in his advertisement.”
While the initial version of CBT-Locker targeted Russian users, variants have spread as criminals continue to purchase and modify the creator’s product. Enter this most recent variant, which graciously offers the victim additional time to pay the ransom, according to SC Magazine. Unfortunately, that’s about the only good news. What makes this one particularly difficult to swallow is the price. While the variants seen in mid-2014 charged a reasonable .02 Bitcoins for the encryption key, this new variant is looking for 3 Bitcoins, which at the time of writing equals US $738. That’s not an easy pill for anyone to swallow, especially when you know you’re paying for your own data.
The variant gives victims 96 hours to pay up. This is a slight variation from the 72 hours users were given when CBT-Locker was discovered in July. So what happens if you don’t pay in the ascribed time? Sure you want to know? If you don’t pay up, then your files become permanently encrypted, says SC Magazine.
The main thing to remember is that this sucker is being distributed via email. Spam campaigns, some distributed through Cutwail, are making their rounds, and all it takes is one misinformed click. Still trust all your users now?
Warn your people, folks. If this is any indication of how 2015 is going to turn out, perhaps we should put our collective minds together and build a time machine.
